I've installed and configured AWS Vault in Windows. In this blog I'll show how to setup MFA, automate token rotation, share AWS Vault with Windows Subsystem for Linux (WSL) and how to do an ECR login on Docker.
Setup MFA
Open up your AWS config file stored at %USERPROFILE%.aws\config and add your MFA serial to your profile:
[profile my_profile]
mfa_serial=arn:aws:iam::123456789012:mfa/mynameThe MFA ARN can be found like this:
- Open AWS Console.
- Go to Identity and Access Management (IAM).
- Select Access Management > Users.
- Open your user.
- Go to the Security credentials tab.
- Copy the ARN from the Assigned MFA device field.
Impersonated accounts
To add the MFA to your impersonated profiles, you can add them like this:
[profile my_dev]
role_arn=arn:aws:iam::987654321012:role/Administrator
source_profile=my_profile
mfa_serial=arn:aws:iam::123456789012:mfa/myname
credential_process=aws-vault exec my_dev --jsonMore on the credential process here.
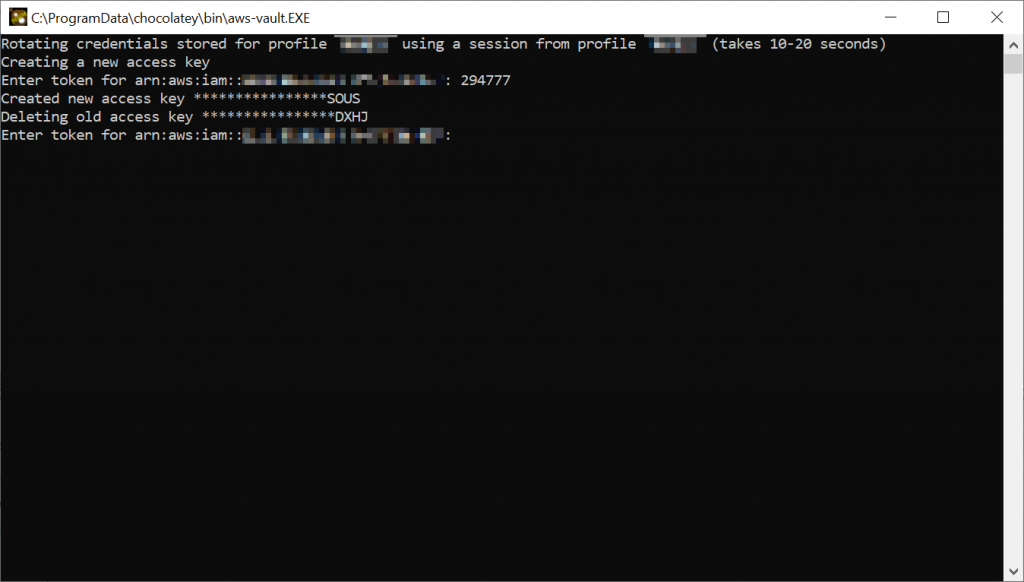
Automate token rotation
I hate it when tokens expire: you need to go into your AWS Console to get a new token, which is just too much hassle. So you need to rotate your token, but I always forget. Let's use the Windows Task Scheduler to remind us to rotate the token:
- Create a Basic Task.
- It should be triggered every month on the second Wednesday at 9:45.
- By triggering it on a second Wednesday it will always be triggered on a work day.
- My token needs to be rotated every 3 months, so technically I can click it away 3 times.
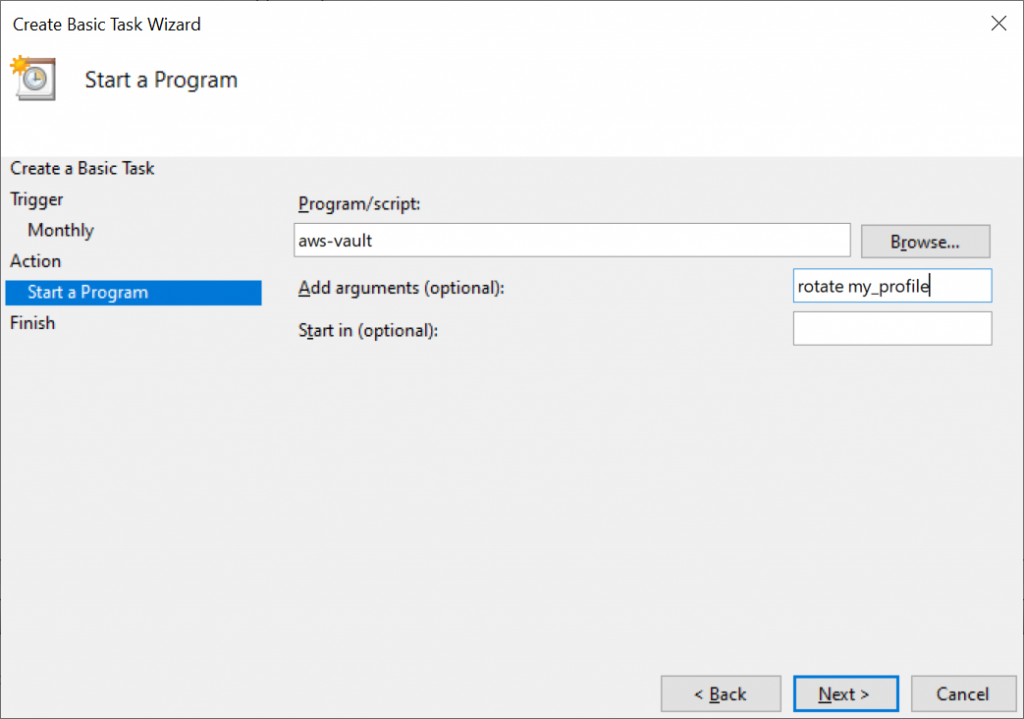
- The program that should be triggered is
aws-vault rotate myprofile.
Here are some screenshots to guide you through:
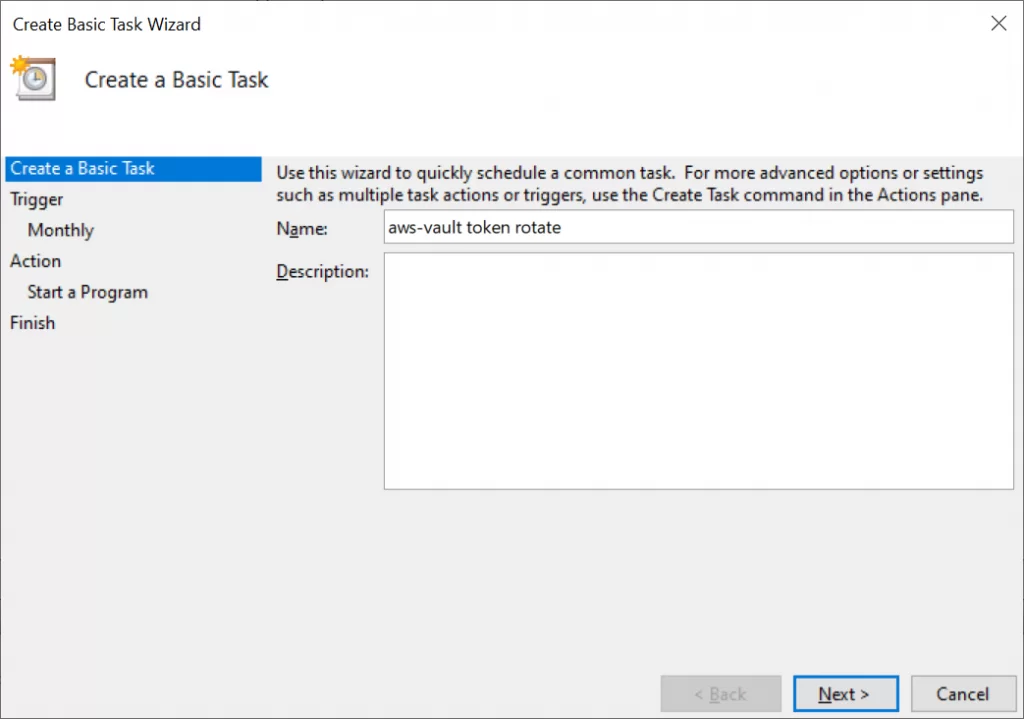
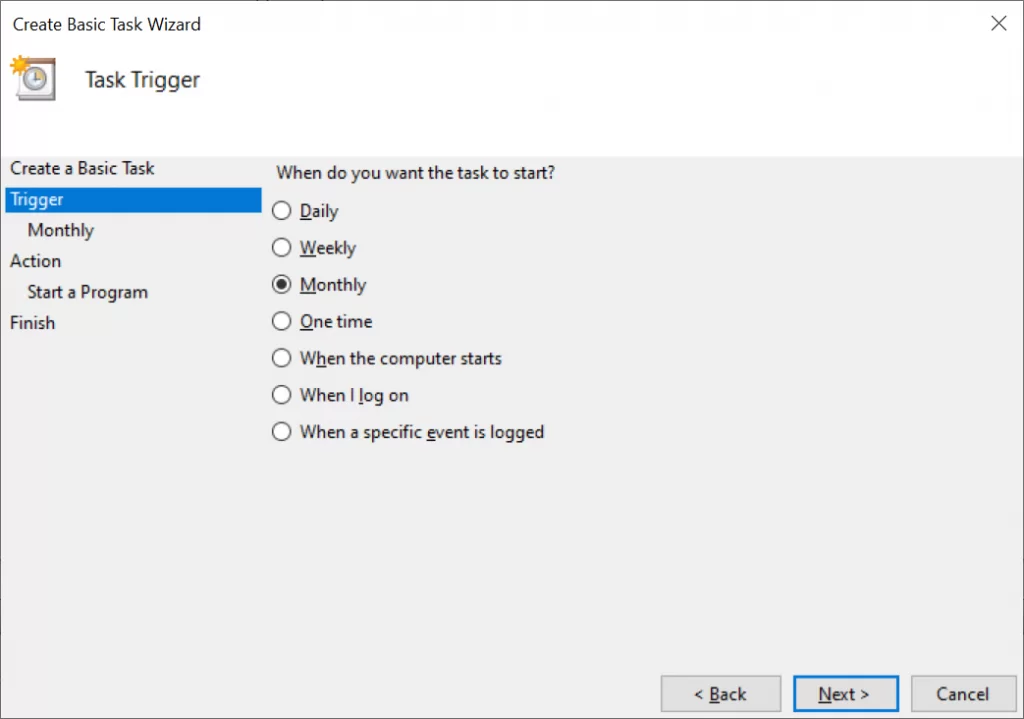
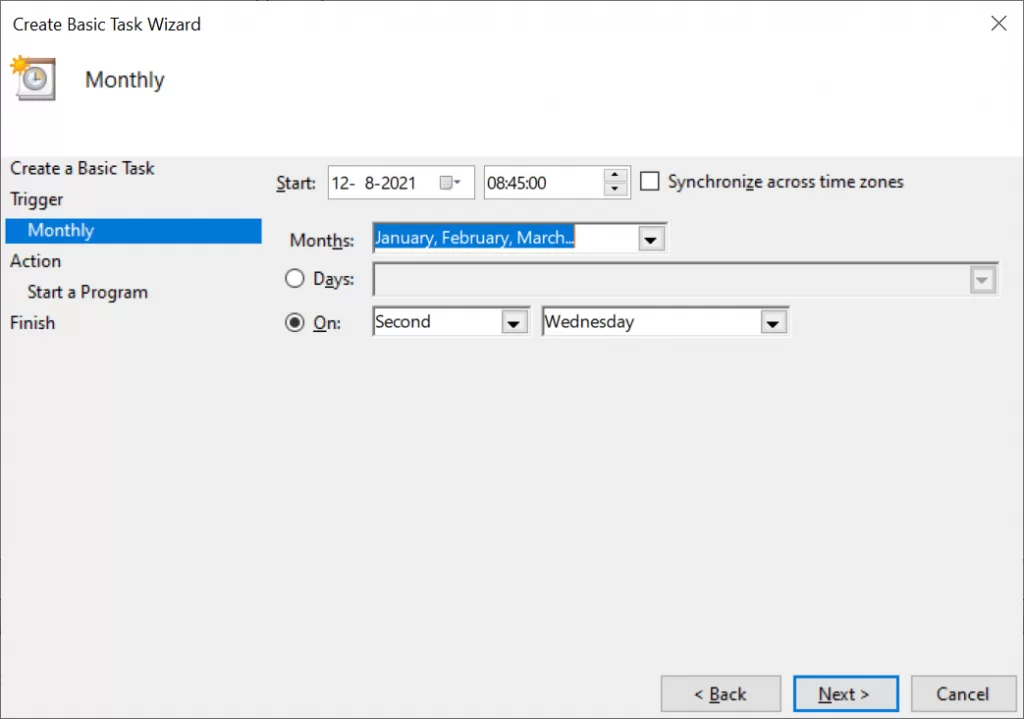
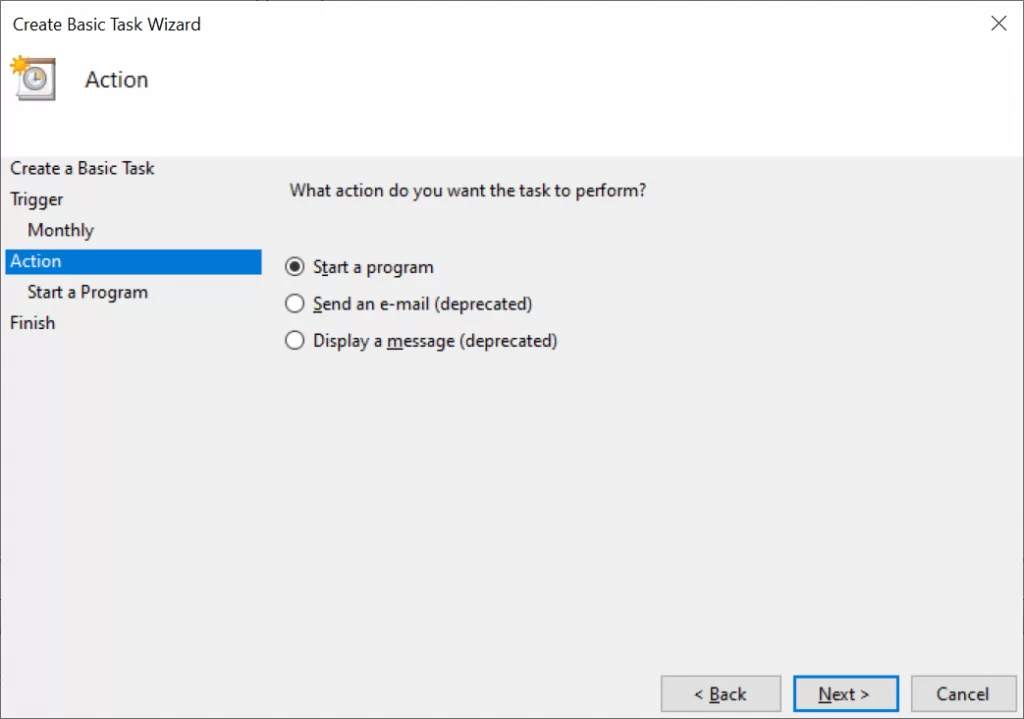
(Re)set AWS token
If you need to reset the key for any reason:
- Go to IAM
- Go to Users
- Select the user
- Click Security credentials tab
- Add access key
- In you terminal do a
aws-vault add [username]and complete the inputs.
Share AWS with WSL
I need to execute some bash scripts which uses account impersonation. I don't want to setup AWS Vault again for Windows Subsystem for Linux (WSL), so let's see how we can link AWS Vault using an alias.
AWS Vault, where art thou?
To locate where AWS Vault is installed on your system, you can execute the following in PowerShell:
Get-Command aws-vaultI installed AWS Vault using Chocolatey, so it is located in the directory C:\ProgramData\chocolatey\bin\aws-vault.exe.
Setup aws-vault alias in WSL
When you open up WSL you'll find out that you can actually run Windows applications from your command-line. In my case this works:
/mnt/c/ProgramData/chocolatey/bin/aws-vault.exe --versionSo the only thing we need to do is setup an alias to access the Windows application:
- Open WSL (using the
wslcommand orbash). - Execute
nano ~/.bash_profileto open (or create) the Bash profile. - Add the path to AWS Vault on a new line:
alias aws-vault="/mnt/c/ProgramData/chocolatey/bin/aws-vault.exe" - Save (ctrl+x and yes).
- Reload the Bash profile:
. ~/.bash_profile - Check if it works by doing:
aws-vault --version.
ECR login
Why did I need this? Well I want to connect AWS Elastic Container Registry (ECR) to Docker. In order to access the it, I need to impersonate my dev account, and retrieve the login for Docker. My script looks like this:
aws-vault exec my_dev \ aws ecr get-login-password --region eu-west-1 | \ docker login \ --username AWS \ --password-stdin 987654321012.dkr.ecr.eu-west-1.amazonaws.comaws-vault exec my_dev ` aws ecr get-login-password --region eu-west-1 | ` docker login ` --username AWS ` --password-stdin 987654321012.dkr.ecr.eu-west-1.amazonaws.com
Works like a charm.
Changelog
- 2023-02-16: Added the (Re)set AWS token section.
- 2021-08-12: Turned the article around a bit and added the Automate Token Rotation.
- 2021-08-10: Added the MFA setup. Added PowerShell command for ECR login.
- 2021-03-08: Initial article.

